Tag: hacking
-

Scammer Revenge: Hunt for Scammers
by
Scam Bait: Exposing Scammers and Their Tactics Scammers are notorious for preying on vulnerable individuals, often targeting the elderly and attempting to steal money through various deceptive means. From phishing schemes to fraudulent investment schemes, scammers stop at nothing to drain their victims’ bank accounts. It’s essential to educate yourself and your family members about…
-

Cybercrime Rapper Sells Stolen Credit Cards
by
Cybercrime Rapper Offers Stolen Credit Cards for Sale This is Punchmade Dev, a rapper who has recently launched an online store selling stolen credit cards. The website also has a glitchy Anonymous mask, and it offers hacked PayPal accounts, credit card details, and “OPSEC software”. The site accepts only cryptocurrency as a mode of payment.…
-
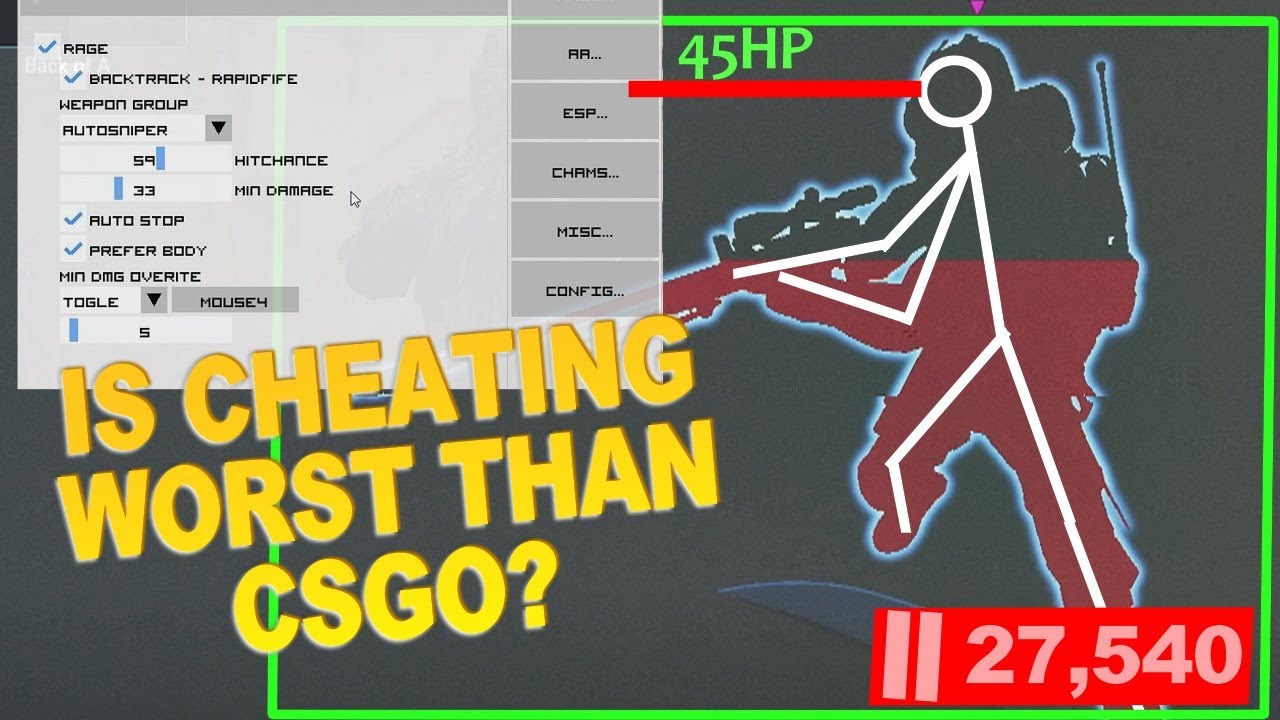
CSGO Cheating on the Rise!
by
CHEATING Is More Prevalent Now Than It was In CSGO! Counterstrike players are noticing a troubling trend in CS2 – an increase in the number of cheaters compared to the previous version, CSGO. A recent incident witnessed by a group of players led them to believe that the cheater problem in the game is escalating.…
-
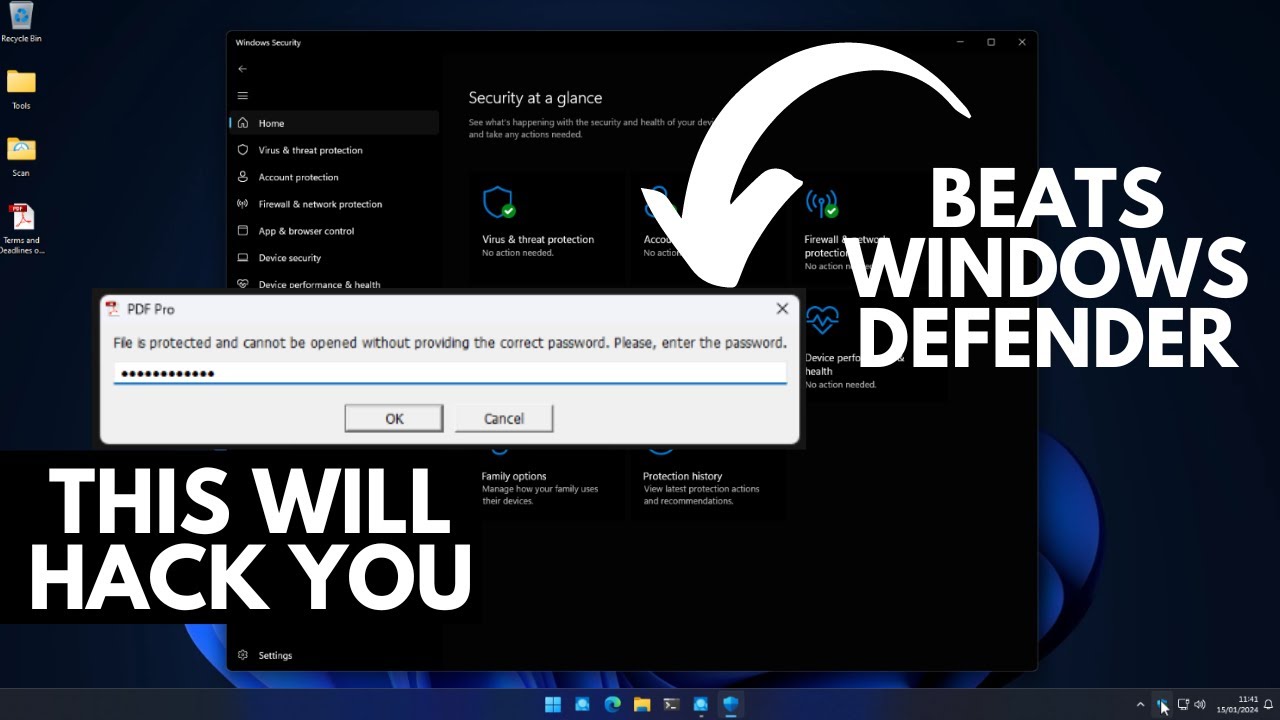
Hacking Windows Defender: Malware Wins
by
Malware vs. Windows Defender: A Look into Infostealer Attacks Malware developers are constantly finding new ways to bypass antivirus software and infiltrate users’ systems —and infostealer malware is no exception. A recent demonstration revealed the effectiveness of infostealer malware delivered via email, showing how it managed to outsmart Windows Defender, a popular antivirus program. Let’s…
-
Sneaky Prank on Noisy Neighbors
by
Loud Neighbors Revenge Prank | HACKING #shorts Sumsub, a company specializing in compliance and anti-fraud solutions, recently shared a viral video on their social media platforms featuring a man using clever tactics to prank his noisy neighbors. The video, labeled as “HACKING #shorts,” showcases the man’s ingenious approach to dealing with the disruptive behavior of…
-

Seytonic Exposes Stuxnet Sabotage
by
A Closer Look at Cyber Espionage, Sabotage, and Hacks of the Digital Age Stuxnet, Pompompurin, and China’s alleged hack of Apple’s Airdrop are making headlines in the world of cyber espionage and digital warfare. Let’s delve into the details of these captivating stories. Revelation of the Stuxnet Saboteur According to a recent report in a…
-
Hacker Tricks NASA with Genius Website Breakdown
by
The NASA Website Was Hacked Using an Exploit in a Database Service Recently, a hacker managed to breach NASA’s website using a vulnerability in a database service. The hacker revealed that the exploit was related to a Dynamic Link Library (DLL), which allowed the execution of shell commands on the server. The Exploit According to…
-
15-Year-Old Hacks NASA & Deletes Files
by
The Astonishing Story of a 15-Year-Old Hacker Have you ever heard an incredible hacking story that sounds almost too unbelievable to be true? Well, get ready to be amazed by the breathtaking tale of a 15-year-old hacker who managed to infiltrate NASA and accidentally deleted their files. A Catastrophic Mistake The young hacker, known as…
-
Billionaire Hacked by Scammers LIVE
by
The Billionaire Hacking Incident: A Shocking Reality Recently, a shocking video surfaced online featuring a hacker who claimed to have successfully hacked a billionaire using a simple phishing attack. The video, which quickly went viral, reveals the ease with which scammers can gain access to personal and sensitive information through deceptive tactics. In the video,…
-

Try Hacking This Password
by
Can You Hack This Password? #shorts Sumsub empowers compliance and anti-fraud teams to combat money laundering, terrorist financing, and online fraud. They have created a password challenge that tests the strength of a password against hacking attempts. The video poses the question, how long would it take for a hacker to crack a particular password?…
-

Sneaky Experiment: Hiring a Real Hacker
by
**Email Hacking Exposed: A Thought-Provoking Journey into Cybercrime** Introduction Have you ever wondered how vulnerable your email account is to hacking? In a recent video experiment, a professional hacker was hired to expose the intricacies of email hacking. The purpose was to illustrate the potential dangers and vulnerabilities in the world of email security, and…
-
Hacking an Entire Company in 40 Minutes
by
Cybersecurity Breach: The 40-Minute Hack #shorts Recently, a shocking video surfaced depicting a hacker infiltrating an entire company’s system in just 40 minutes through a social engineering attack. Sumsub, a company dedicated to empowering compliance and anti-fraud teams, was the unfortunate target of this cybersecurity breach. The video showcases the hacker’s ability to exploit human…
-
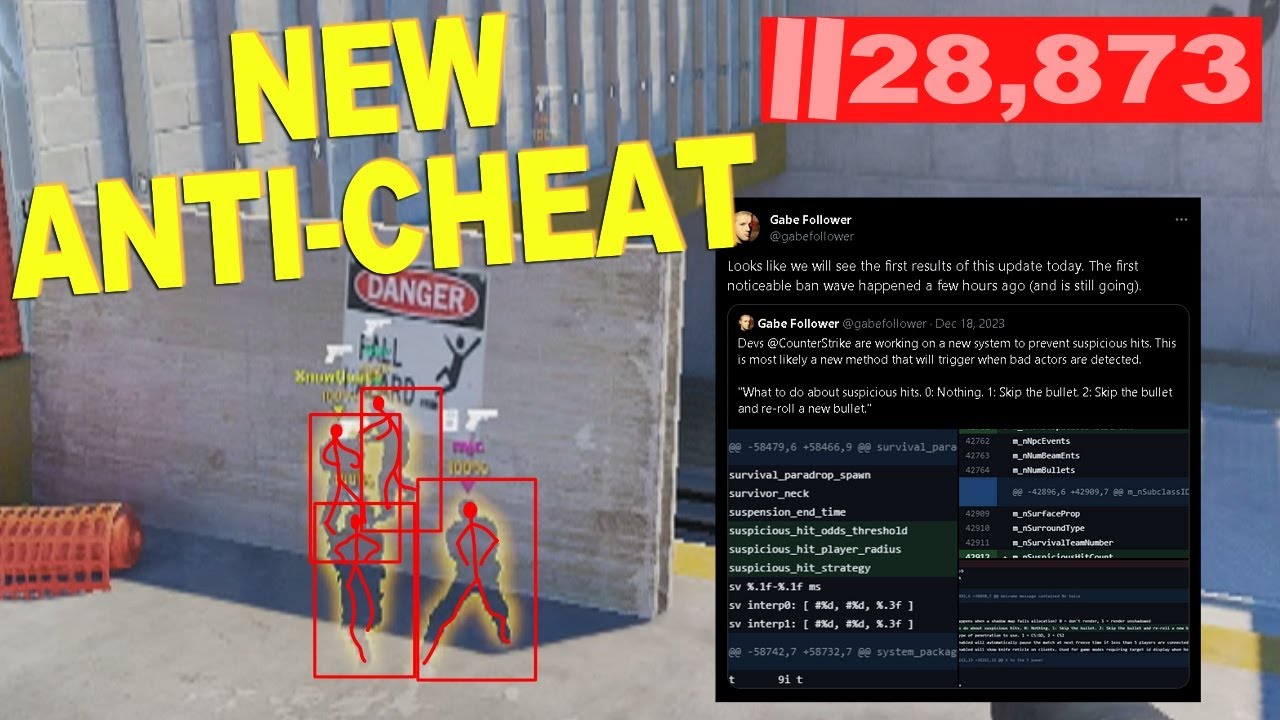
Cheating Valve’s Anti-Cheat! (Update Results)
by
The Battle Against Cheating in Premier Mode Valve recently updated its anti-cheat system to better detect cheaters, resulting in a massive VAC wave. The community is now eager to see if these changes will effectively eliminate cheating in Premier mode. Five players have been flagged as potential cheaters, and their profiles have sparked a heated…
-
Unleashing Chaos: Hacking Discord with a Link
by
Hacking a Discord Server With a Link! The End of Innocence Hackers and scammers are constantly finding new ways to exploit online platforms, and Discord is no exception. Recent events have revealed a striking vulnerability in Discord servers—a vulnerability that can be exploited with just a single click on a link. For anyone who has…
-

Death Valley Drive: 24-Hour USA Road Trip!
by
Experience the Diverse Scenery of the USA Join Leo behind the scenes on his journey from Las Vegas to the Mammoth Lakes in California, passing through Death Valley. Experience the unique landscapes ranging from desert to snow-capped mountains in a single day. The drive-through Death Valley offers a once-in-a-lifetime experience that Leo and his companions…
-
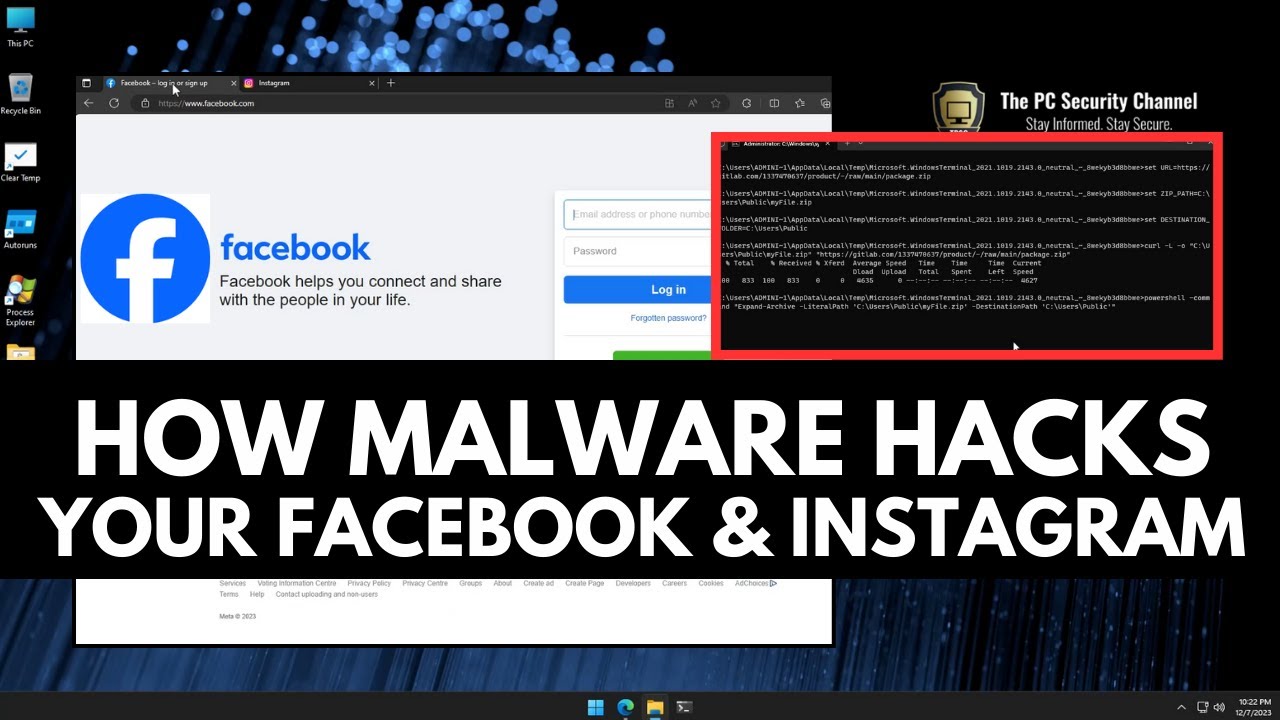
Hacking Facebook & Instagram with Malware
by
Understanding How Facebook & Instagram Accounts Are Hacked by Malware Today, we’re going to explore the chilling behind-the-scenes process of how cyber attackers can infiltrate your Facebook and Instagram accounts using a malicious software known as Infostealer Malware. This software thrives on false messages and attempts to steal your session tokens or passwords, giving hackers…