Malware vs. Windows Defender: A Look into Infostealer Attacks
Malware developers are constantly finding new ways to bypass antivirus software and infiltrate users’ systems —and infostealer malware is no exception. A recent demonstration revealed the effectiveness of infostealer malware delivered via email, showing how it managed to outsmart Windows Defender, a popular antivirus program. Let’s delve into the details of this attack and explore the potential risks it poses to individuals and businesses.
The Inside Story of an Infostealer Attack
The attack begins innocuously with an email, often disguised as a legitimate request or offer. This initial email is a ploy to engage the recipient in a conversation and build a sense of trust. After establishing a rapport, the attacker sends a follow-up email containing a link to a seemingly harmless website. The website appears legitimate, with no immediate signs of malicious intent.
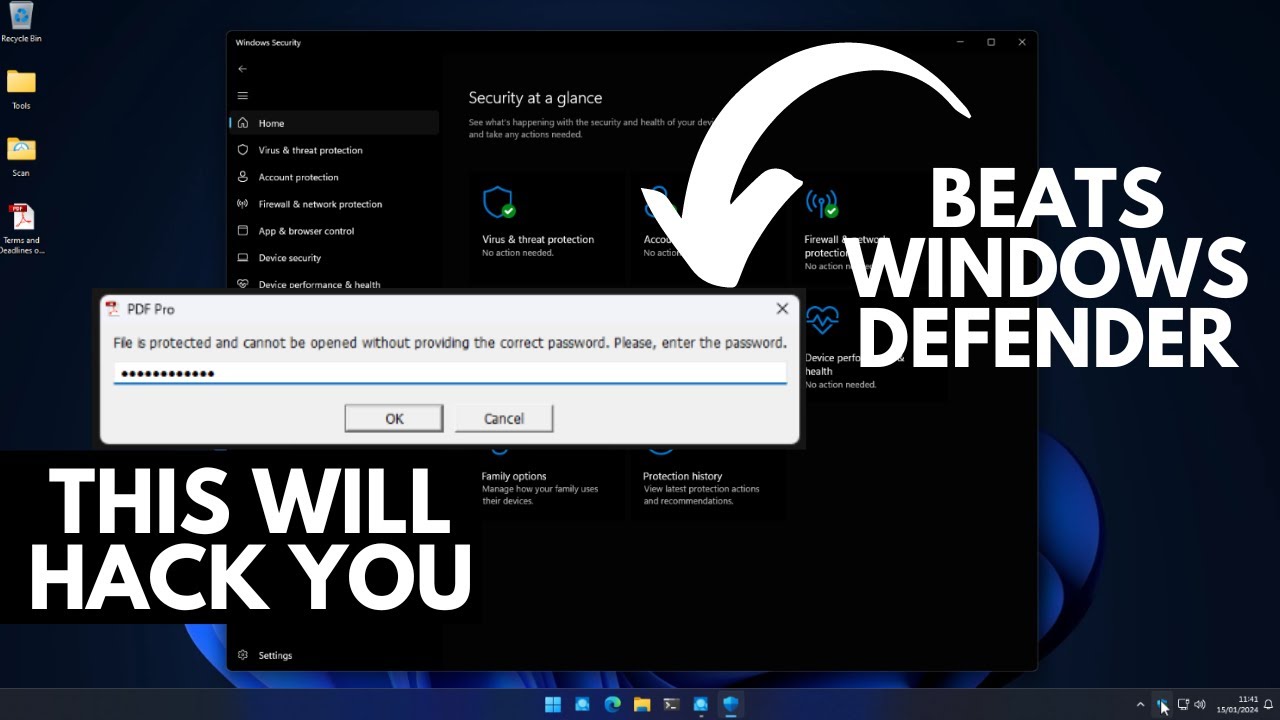
Upon visiting the website, the user is prompted to download a file, usually in a compressed format. What makes this attack particularly insidious is the use of a multi-stage extraction process. The compressed file contains seemingly innocuous content, such as images and videos, alongside a password-protected PDF file. Once the victim enters the password, the malware is unleashed, silently capturing sensitive information from the user’s system.

Defying Windows Defender: The Anatomy of the Attack
Despite the presence of an active and updated Windows Defender, the infostealer malware successfully evades detection. The sophistication of this attack lies in its ability to bypass traditional antivirus screening, primarily through obfuscation and password protection mechanisms. In this display of evasive tactics, it becomes evident that conventional antivirus tools are ill-equipped to counter such advanced threats.
While an alternative antivirus solution may detect the malware based on its reputation, the challenge persists in confronting these threats preemptively. This raises alarms on the necessity for users to exercise heightened situational awareness and vigilance in the face of evolving cyber threats.
The Ripple Effect of Stolen Data
Once the infostealer malware succeeds in its mission, it exfiltrates the stolen data to the attackers’ command and control servers. The compromised information may then be sold on the dark web, where it becomes part of a thriving marketplace for stolen credentials and personal data. The implications of such a breach extend beyond the immediate victim, potentially impacting various aspects of their digital presence.
Moreover, the attack serves as a cautionary reminder of the need for continuous monitoring and proactive measures to mitigate potential fallout from a security breach. Changing passwords, logging out of sensitive accounts, and enhancing security protocols become imperative steps for individuals and organizations in safeguarding their digital assets.
Powering Up with Flare: Shedding Light on Dark Web Exposure
Amid the unsettling realities of dark web activities, tools like Flare present a valuable resource to gauge one’s exposure and proactively address potential compromises. Flare’s platform offers the capability to search for leaked data and instances of dark web mentions, empowering users to take control of their digital footprint.

A powerful demonstration of Flare’s capabilities revealed the shocking prevalence of leaked credentials, illustrating the urgent need for comprehensive measures to combat cyber threats. By leveraging Flare’s insights, individuals and businesses gain the means to identify and counteract potential vulnerabilities, ultimately fortifying their cybersecurity posture.
Empowering Users in the Fight Against Cyber Threats
Amid the ever-present specter of cyber attacks, knowledge and awareness emerge as key weapons in safeguarding against potential breaches. By staying informed and equipping oneself with robust security practices, individuals and organizations can effectively fortify their defenses and navigate the digital landscape with confidence.
As we confront the evolving landscape of cyber threats, embracing continuous learning and proactive measures emerges as an imperative. Together, with a collective commitment to cybersecurity, we embark on a journey to fortify our digital realms and uphold the integrity of our online experiences.
Remember: vigilance today is the guardian of a secure tomorrow.
Stay informed, stay secure.

Author: [Your Name]
Date: [Date]
Word Count: [Word Count]