Tag: cyber security
-

Apex Legends Security Breach!
by
The Shocking Incident: Apex Legends Hacked Live During Global Series In a jaw-dropping turn of events, Apex Legends, one of the most popular battle royale games, was hacked live during a global esports series, leaving audiences and players stunned. The breach occurred during one of the largest tournaments, raising concerns about the game’s security and…
-
Sneaky Ransomware Story ft. Joe Biden
by
Ransomware Incidents Gain Attention with Reference to Joe Biden and The PC Security Channel Instances of ransomware attacks have been on the rise, with cybercriminals constantly finding new ways to exploit vulnerabilities and disrupt systems. Recently, a new ransomware dubbed “Biden” has caught the attention of researchers, including MalwareHunterTeam and The PC Security Channel. The…
-
Mastering Cybersecurity Basics
by
Cybersecurity Skills: A Beginner’s Guide In a world where cyber threats lurk around every virtual corner, having basic cybersecurity skills can be a game-changer. The video “Cybersecurity for Beginners: Basic Skills” delves into essential approaches and investigative techniques to shield yourself from scams, malware, ransomware, and other online dangers. Let’s break down some key takeaways…
-
Windows Defender Tries to Stop Ransomware
by
Windows Defender vs Ransomware 2024 Every year, the battle between Windows Defender and ransomware takes center stage as security enthusiasts eagerly await the outcome. The testing in 2024 promises to be as intense as ever, with tweaks to Attack Surface Reduction (ASR) using Defender UI and default settings. The question on everyone’s mind is whether…
-
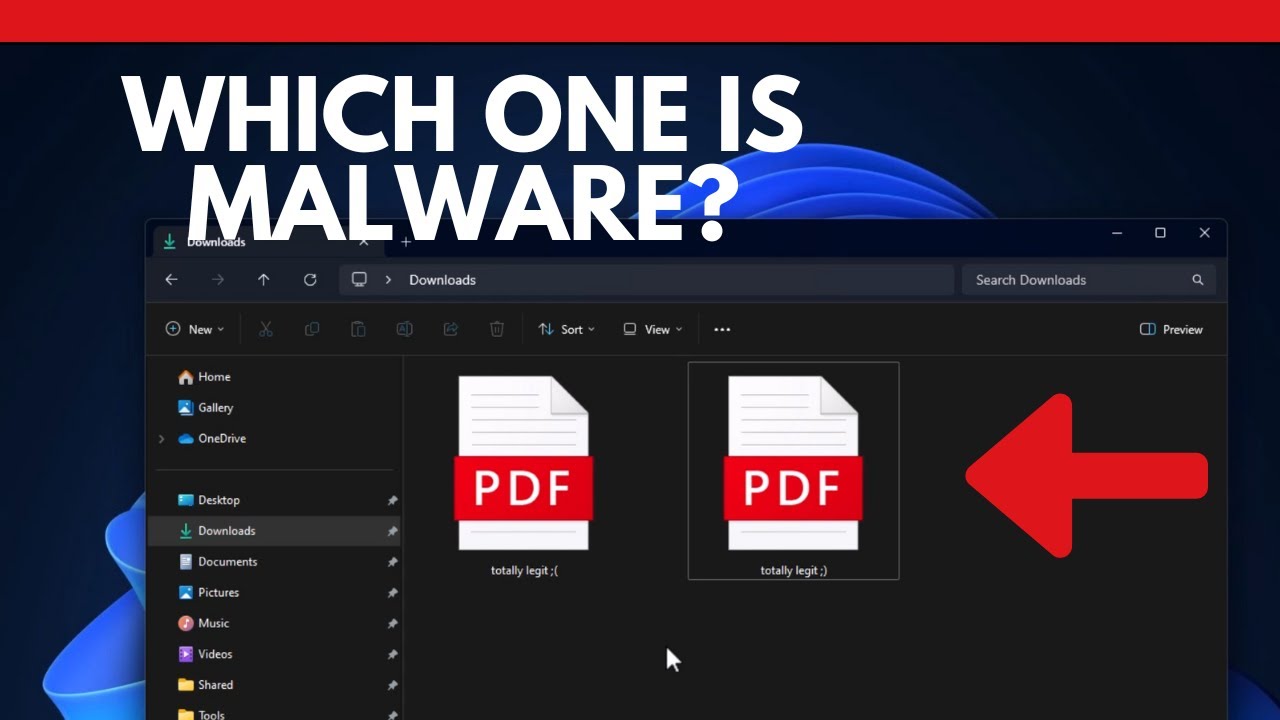
Hack Your Windows: Avoiding Malware Risk
by
Protect Yourself from Malware with These Windows Tweaks Understanding the Threat Most users fall victim to malware by accidentally running malicious files disguised as harmless documents like PDFs or contracts. The consequences can be dire, leading to data loss or ransomware attacks. But fear not, there are simple Windows tweaks that can help you avoid…
-

Malware Infiltrates Major YouTubers
by
Malware Alert: YouTube Channels Spreading Dangerous Viruses! YouTube Channels Hacked, Spreading Malware The PC Security Channel has uncovered a troubling trend involving large YouTube channels being hacked and used to spread malware. Channels with hundreds of thousands of subscribers are being manipulated to distribute dangerous viruses. The attacks are usually in the form of videos…
-

3 Million Hacked Toothbrushes Cause DDoS Attack!
by
3 Million Hacked Toothbrushes, FBI Nukes Chinese Government Botnet, and Italian Hackers Weaponize Pizza Reports surfaced alleging that 3 million electric toothbrushes were hacked, added to a botnet, and deployed for DDoS attacks. However, the reality of this sensational news required closer examination. While smart toothbrushes have increasingly become common, they are often not directly…
-
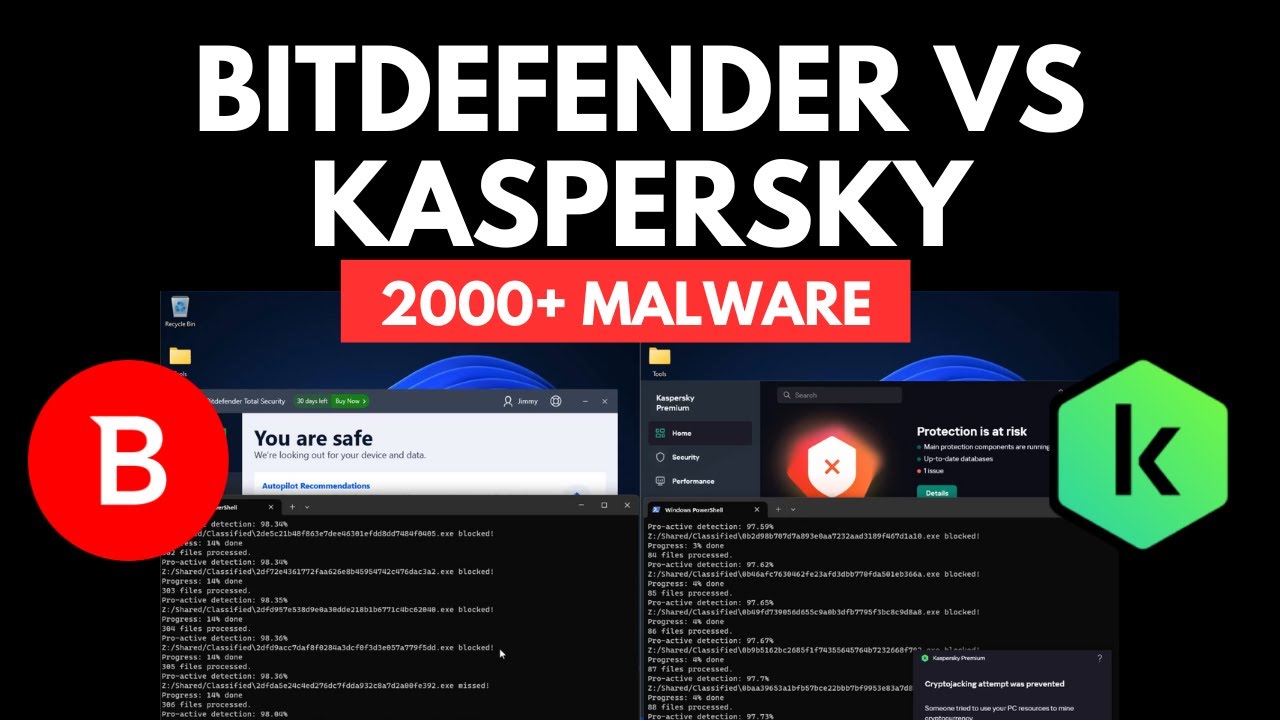
Ultimate Battle: Kaspersky vs Bitdefender vs 2000 Malware
by
Kaspersky vs Bitdefender: Battle of the Antivirus Titans Hello everyone! Today, we have an exciting showdown between two heavyweights in the cybersecurity world: Kaspersky and Bitdefender. We are going to pit these two security products against each other in a rigorous test involving over 2000 malware samples. Sit tight, this is going to be intense!…
-

Cybercrime Rapper Sells Stolen Credit Cards
by
Cybercrime Rapper Offers Stolen Credit Cards for Sale This is Punchmade Dev, a rapper who has recently launched an online store selling stolen credit cards. The website also has a glitchy Anonymous mask, and it offers hacked PayPal accounts, credit card details, and “OPSEC software”. The site accepts only cryptocurrency as a mode of payment.…
-
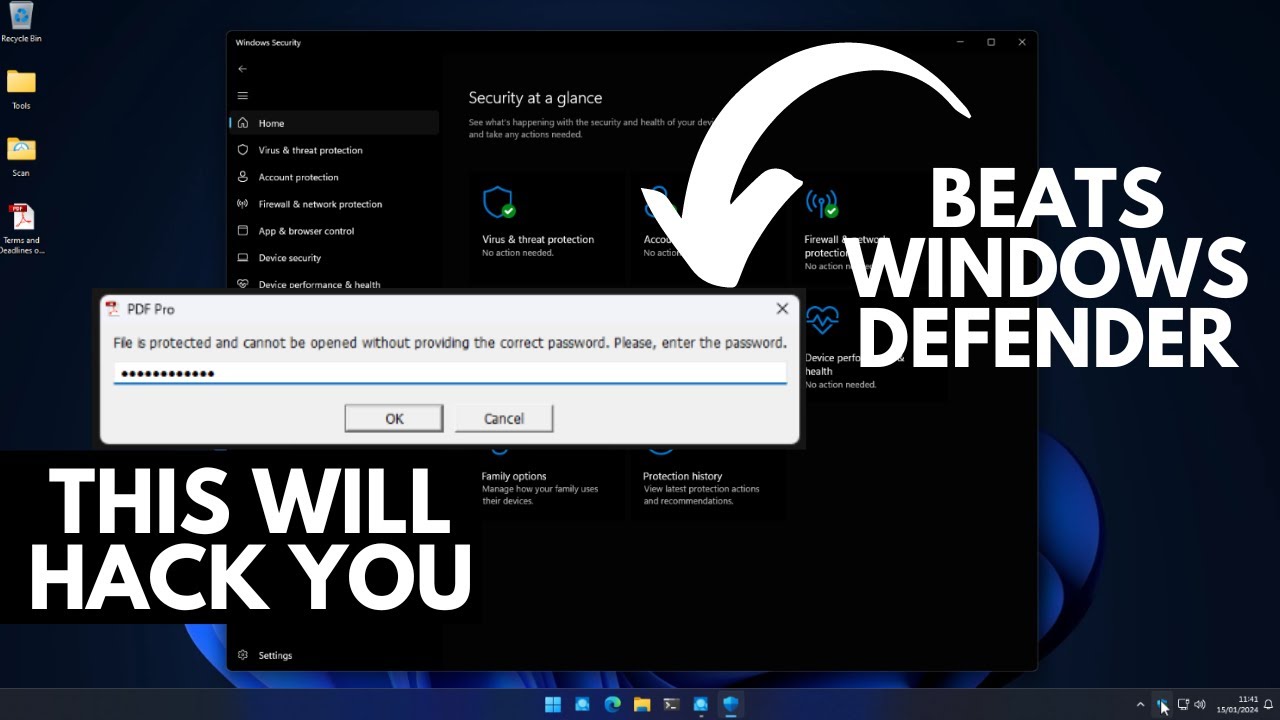
Hacking Windows Defender: Malware Wins
by
Malware vs. Windows Defender: A Look into Infostealer Attacks Malware developers are constantly finding new ways to bypass antivirus software and infiltrate users’ systems —and infostealer malware is no exception. A recent demonstration revealed the effectiveness of infostealer malware delivered via email, showing how it managed to outsmart Windows Defender, a popular antivirus program. Let’s…
-

Seytonic Exposes Stuxnet Sabotage
by
A Closer Look at Cyber Espionage, Sabotage, and Hacks of the Digital Age Stuxnet, Pompompurin, and China’s alleged hack of Apple’s Airdrop are making headlines in the world of cyber espionage and digital warfare. Let’s delve into the details of these captivating stories. Revelation of the Stuxnet Saboteur According to a recent report in a…
-
Mastering Account Security: My Strategy
by
My FULL Account Security Strategy Explained Account security is a critical aspect of using the internet, and Josh from All Things Secured has developed a comprehensive strategy over the years. His strategy follows seven laws, shaping how he approaches each of his online accounts, from social media platforms to bank accounts and everything in between.…
-

2024 Online Security Q&A LIVE!
by
I hope you enjoyed the conversation on online security and privacy. Thank you for joining the live stream and contributing your questions and comments. It’s been a pleasure. Stay safe and take care!
-

Is Privacy Dead in 2024? 7 Wild Predictions
by
Privacy Predictions for 2024: What’s Coming for Your Cybersecurity? As the world continues to embrace artificial intelligence, quantum computing, and biometrics, what does this mean for your online privacy and security? In this article, we delve into seven key predictions for 2024 that could significantly impact your digital life. Artificial Intelligence & Privacy AI has…
-

Death Valley Drive: 24-Hour USA Road Trip!
by
Experience the Diverse Scenery of the USA Join Leo behind the scenes on his journey from Las Vegas to the Mammoth Lakes in California, passing through Death Valley. Experience the unique landscapes ranging from desert to snow-capped mountains in a single day. The drive-through Death Valley offers a once-in-a-lifetime experience that Leo and his companions…
-
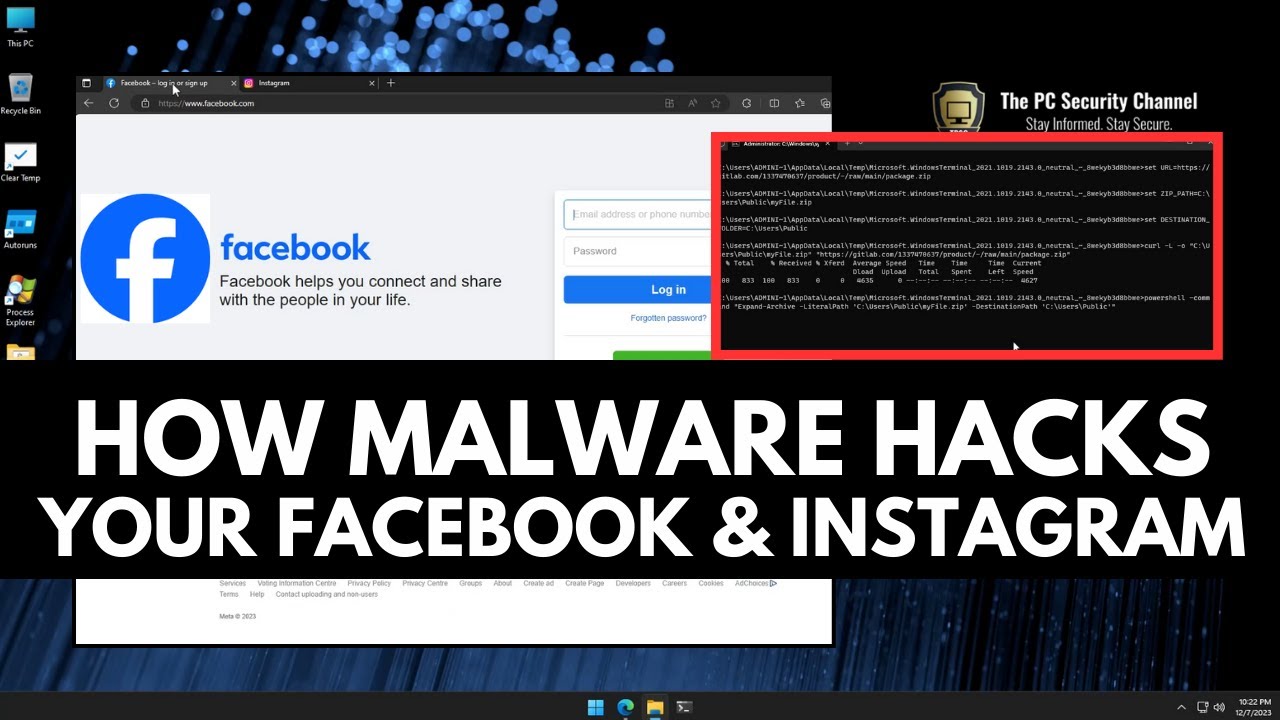
Hacking Facebook & Instagram with Malware
by
Understanding How Facebook & Instagram Accounts Are Hacked by Malware Today, we’re going to explore the chilling behind-the-scenes process of how cyber attackers can infiltrate your Facebook and Instagram accounts using a malicious software known as Infostealer Malware. This software thrives on false messages and attempts to steal your session tokens or passwords, giving hackers…