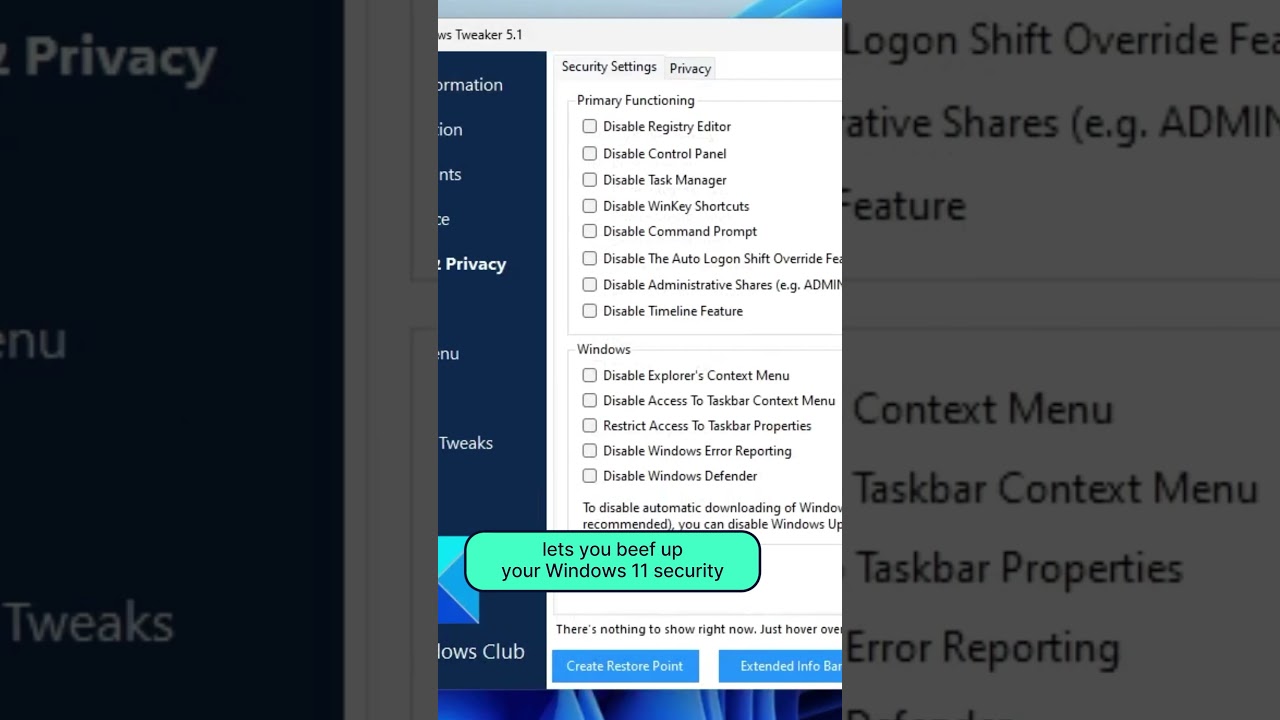
Tag: hacking
-

Cracking the Casino Code: Math vs Odds
by
The eternal struggle between the chaos of probability and the soberness of calculation has been the focus of many individuals throughout history. From Mick Jagger’s ancestor to modern-day lottery winners, the battle between math and fortune continues to spark intrigue and curiosity. The ups and downs of gambling have given rise to legendary tales of…
-
Incredible Casino Hack: 1980 Exposed
by
The Monkey Paw: A Tale of Casino Fraud Have you ever heard of the monkey paw, a small but powerful device that managed to hack a casino for millions of dollars in the 1980s? The story of its creator, Tommy Carmichael, is a fascinating one filled with deceit, ingenuity, and ultimately, justice. The Ingenious Monkey…
-
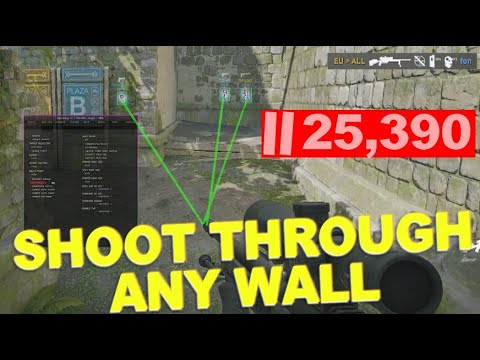
Hacks: Shoot Through Any Wall!
by
Cheats Are So Advanced They Can Shoot Through Any Wall! As the gaming world continues to evolve, so do the cheats. CS2 players are experiencing cheats that are more advanced than ever before – to the extent that they can shoot through any wall! 🎮 An Unbelievable Gameplay Experience The narrator, known as Times, recently…
-
The Truth About AI’s End
by
Demystifying the Doom and Gloom: AI and Public Perception When it comes to the public narrative about artificial intelligence, the stories of doom and gloom can be a bit misleading. From the perspective of experts, the fear surrounding AI is steeped in society and perpetuated by the deep-seated concern of nonhuman intelligence taking over and…
-
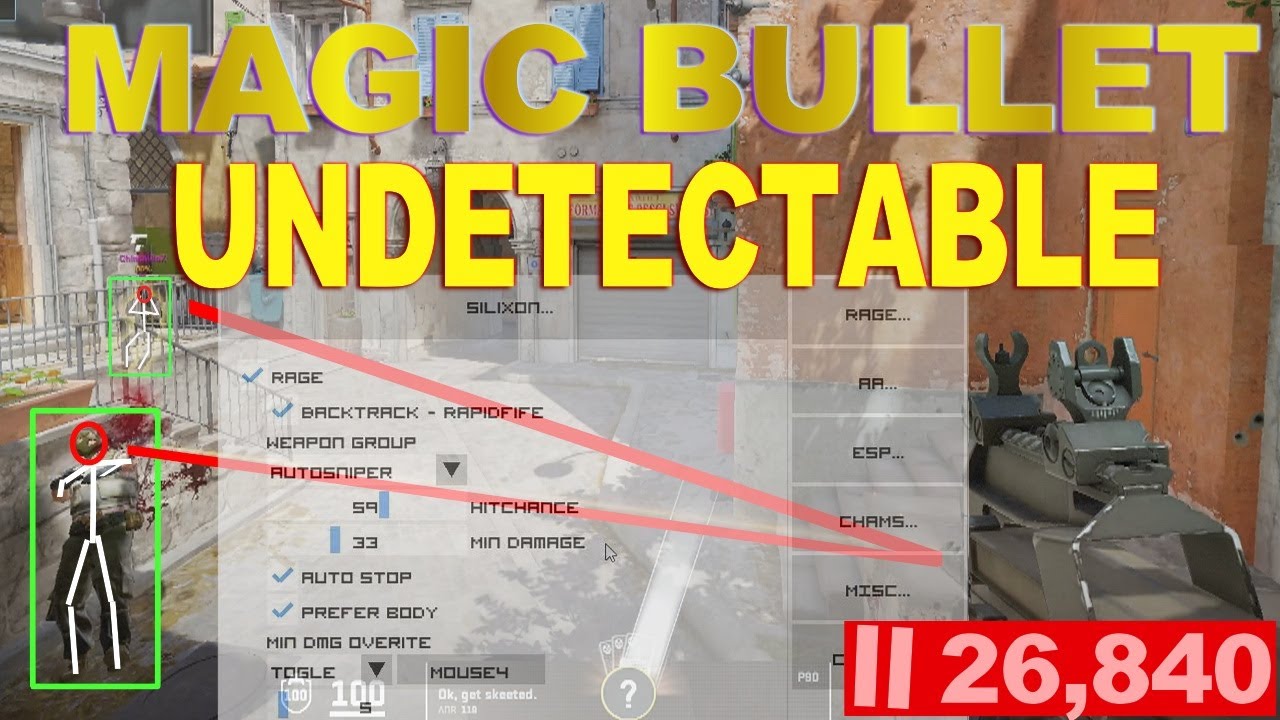
Untraceable Magic Bullet Cheating in Premiere!
by
Cheating In Premier with Magic Bullet is Undetectable! The Shady Underbelly of Premier Play The world of Premier CS:GO play has always been a hotbed for cheating allegations. In a recent game, a player noticed something suspicious with an opponent’s ELO score. The subsequent investigation revealed some surprising evidence of cheating 🕵️ Unearthing the Evidence…
-

Hacker Takes Down Internet in 30 Mins
by
Joe Grand: From Hacker to Ethical Superhero Joe Grand, once a notorious hacker, has transformed into a real-life ethical superhero. His journey from delinquent hacker to a force for good is an inspiring story of redemption and dedication to helping others. Let’s dive into the details of Joe’s incredible transformation and how he uses his…
-

Malware Infiltrates Major YouTubers
by
Malware Alert: YouTube Channels Spreading Dangerous Viruses! YouTube Channels Hacked, Spreading Malware The PC Security Channel has uncovered a troubling trend involving large YouTube channels being hacked and used to spread malware. Channels with hundreds of thousands of subscribers are being manipulated to distribute dangerous viruses. The attacks are usually in the form of videos…
-

3 Million Hacked Toothbrushes Cause DDoS Attack!
by
3 Million Hacked Toothbrushes, FBI Nukes Chinese Government Botnet, and Italian Hackers Weaponize Pizza Reports surfaced alleging that 3 million electric toothbrushes were hacked, added to a botnet, and deployed for DDoS attacks. However, the reality of this sensational news required closer examination. While smart toothbrushes have increasingly become common, they are often not directly…
-
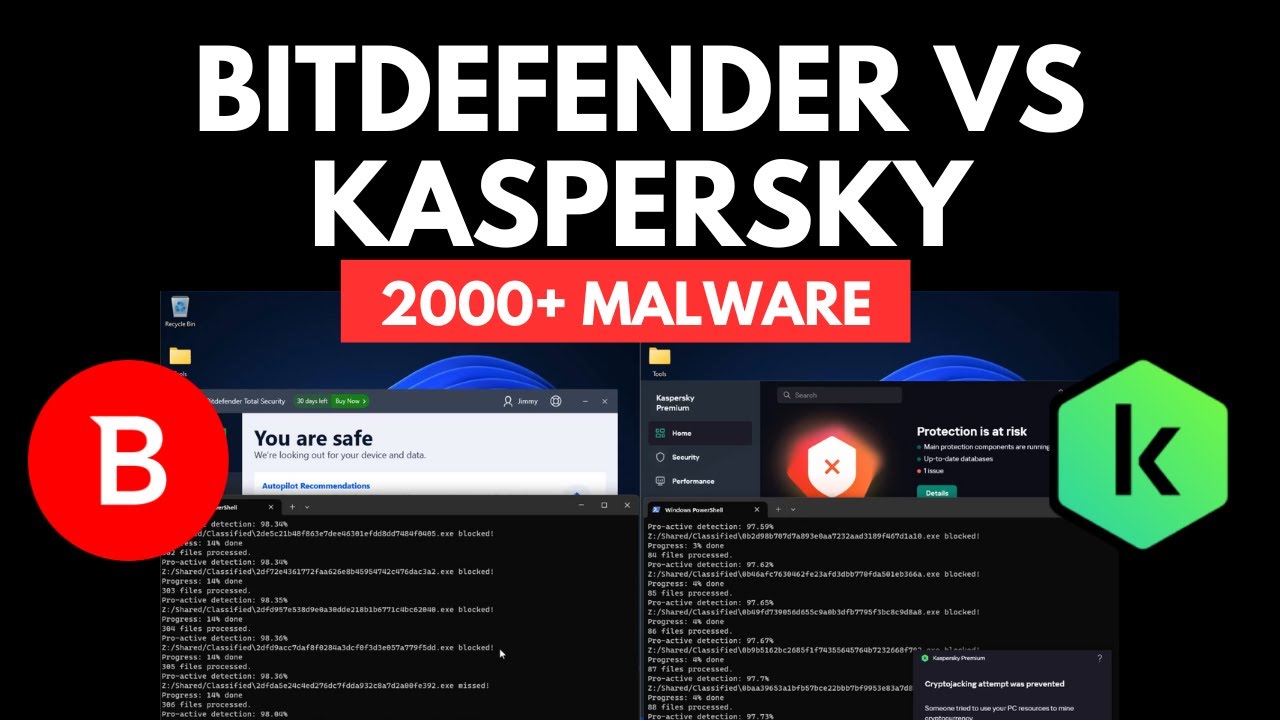
Ultimate Battle: Kaspersky vs Bitdefender vs 2000 Malware
by
Kaspersky vs Bitdefender: Battle of the Antivirus Titans Hello everyone! Today, we have an exciting showdown between two heavyweights in the cybersecurity world: Kaspersky and Bitdefender. We are going to pit these two security products against each other in a rigorous test involving over 2000 malware samples. Sit tight, this is going to be intense!…
-

ATM Skimmer Hack Revealed!
by
The Problem of ATM Skimming: A Closer Look ATM skimming is a serious problem that affects millions of people around the world. Criminals use skimming devices to steal sensitive information from unsuspecting ATM users, putting their financial security at risk. Understanding how these devices work is essential for protecting oneself from fraud. Read on to…
-

Sumsub Hacker Strikes: Change Your Passwords Now!
by
Protecting Your Online Security When a security researcher from Canada stumbled upon a leaked password from an unknown individual, they immediately reached out to warn the person about the potential risks. This unexpected encounter with a white hat hacker shed light on the importance of maintaining strong password security in an era dominated by cyber…
-

Savage Prank: Hacking Scammers
by
Scammer File Deletion Exposé | Hacking Scammers Reactions The Menace of Scammers Scammers are heartless individuals who prey on the vulnerable, especially the elderly, to siphon money from bank accounts. They are not above resorting to deceptive tactics like phishing scams and credit card fraud for personal gain. Such tactics include: 1. Accessing Bank Saving…
-

Uncovering ATM Skimmer in Vienna
by
Finding an ATM Skimmer: A Cautionary Tale While using an ATM machine in Vienna, a vigilant individual discovered a potential skimmer device attached to the machine. This incident serves as a sobering reminder to always be wary of cyber threats and to remain proactive in safeguarding personal information. An Unsettling Discovery Upon approaching the ATM,…
-
Uncovering the Real ‘Wolf of Wall Street’ Fraudster
by
The Truth Behind ‘The Wolf of Wall Street’ 🎥 Did you know that the blockbuster film ‘The Wolf of Wall Street’ was funded by one of the biggest anti-money laundering and corruption cases in history? Let’s dive into the shocking truth behind the world’s biggest financial fraud and the real fraudster who made it all…
-
ATM Hackers: How They Did It
by
The Circuit Board that Hacked 7 ATMs Introduction The use of a simple electronic circuit board to hack seven ATMs has caused quite a stir in the security and financial worlds. This method is an ingenious yet alarming example of how technology can be exploited for criminal activities. The Hack Criminals bypassed the physical security…
-

Hiring a Real Hacker to Hack Our Email
by
Delving into the World of Email Hacking In a daring and eye-opening experiment, a team of professionals took the plunge into the intricate world of email hacking. Through a controlled and informative demonstration, they sought to highlight the potential dangers and vulnerabilities in the realm of email security. Setting the Trap The team’s strategy involved…