Tag: online security
-
Scammers Exposed: Number Spoofing Trick!
by
Unveiling the Tactics of Scammers: How Your Number is Spoofed Have you ever received a call from a familiar number, only to realize that the person on the line is not who they claim to be? This deceptive practice, known as spoofing, is on the rise as scammers use advanced technology to manipulate caller IDs…
-
Exposing Voice Scam Tactics
by
How scammers use AI to fake your voice In today’s digital age, scammers are becoming increasingly sophisticated in their tactics to deceive unsuspecting individuals. One prevalent method used by scammers is the manipulation of voice recordings to make it seem like they are speaking with a trusted individual. But how exactly do they achieve this…
-

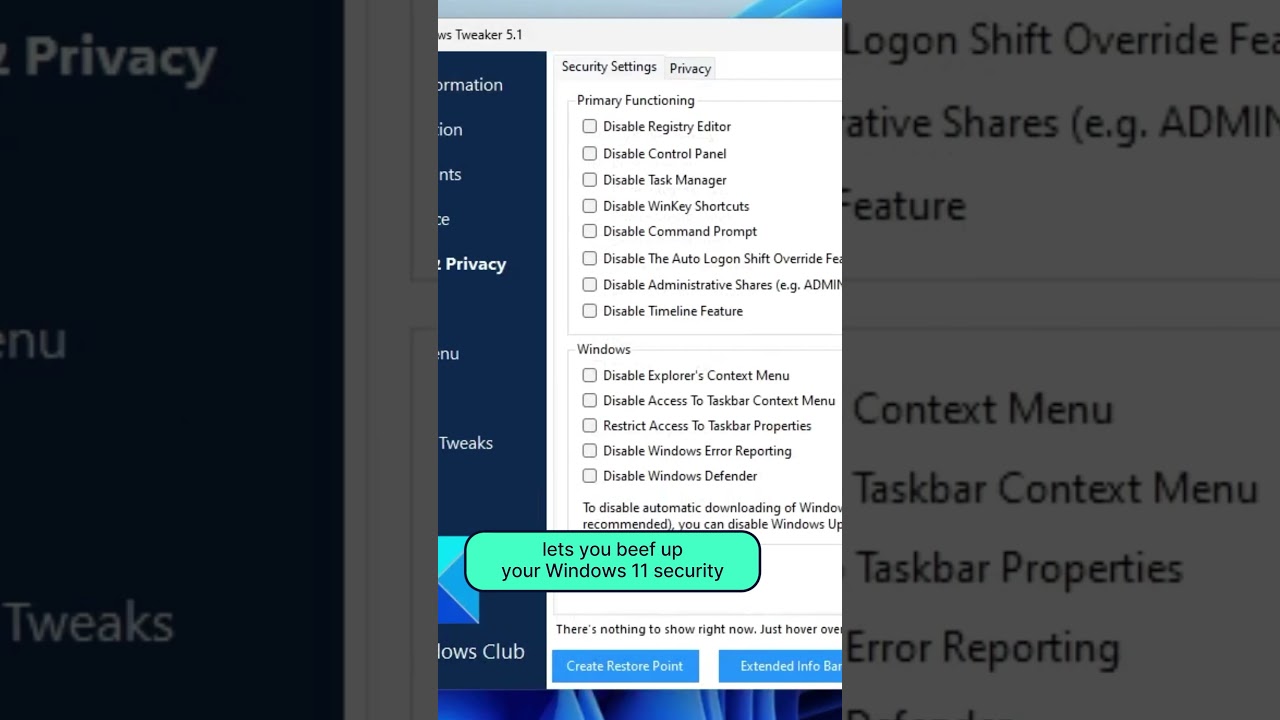
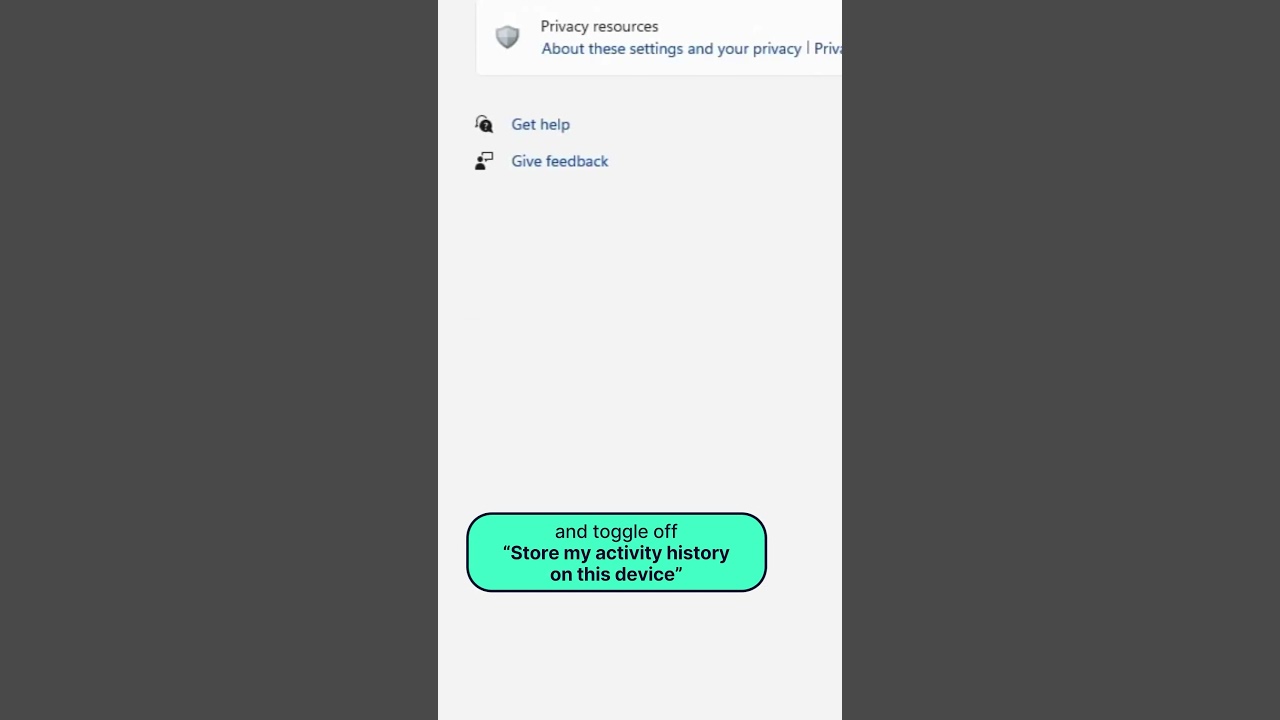
The Ultimate Privacy & Security Toolbox
by
Privacy & Security: The Essential Tech Stack 🔐 In the age of widespread online threats, safeguarding personal data has become crucial. Users like Josh have crafted powerful privacy and security stacks to shield their information against prying eyes. Let’s delve into the 12 tools he employs daily to fortify his digital presence. Password Manager: 1Password…
-

Store Gets Hacked by Sumsub Scammer
by
Scammer Hacks the Store: An Insight into Cybersecurity Threats The Vulnerability The recent revelation from Sumsub sheds light on the alarming vulnerability faced by online stores. An attacker can exploit a QR code and SQL injection to manipulate the product prices and even lock the entire store by deleting items from the database. This dangerous…
-

Master Hacker Controls 26k Tubs Worldwide
by
Controlling over 26,000 Hot Tubs Worldwide: A Modern Technological Marvel! In a fascinating turn of events, a talented individual has managed to hack and control over 26,000 hot tubs across the world. These luxurious hot tubs, equipped with a mobile app for remote control, are now under the adept manipulation of this tech-savvy individual. Through…
-

Insane Android QR Code Hack?!
by
The Power of Hacking with an Android Phone and QR Codes In the world of hacking, ingenuity knows no bounds. Forget the stereotypical image of a hacker behind a massive computer setup. Today, all it takes is an ordinary Android phone, a bit of know-how, and a devious mind to wreak havoc. Sumsub, a company…
-

Ditch the Rules: Security Tips to Ignore!
by
The Importance of Building a Personalized Threat Model When it comes to cybersecurity, the sheer volume of advice and best practices available can be overwhelming. How do you know what advice to follow and what to ignore? Josh from All Things Secured and Henry from Techlore believe that the key lies in building a personalized…
-
Billionaire Gets Hacked by Sumsub
by
Breaking Into a Billionaire’s Account Imagine a world where even billionaires are not safe from cyber attacks. In a recent #shorts video, we witness how a group of individuals managed to hack into a billionaire’s account with disturbing ease. The Hack The team consists of a human hacker and a technical expert. They leverage information…
-

Sumsub Mitnick Hacks Paris Hotel Safe
by
Kevin Mitnick’s Paris Hotel Safe Break-In Revealed in #Shorts Unveiling Hotel Safe Security Risks Kevin Mitnick, renowned for his prowess in hacking and security, recently shared a startling discovery during his stay at a luxurious Parisian hotel. Concerned about carrying a substantial amount of cash in the bustling city, Mitnick opted to secure it in…
-

Hacking QR Codes: The Dirty Truth
by
Decoding the World of QR Codes Unraveling the Mysteries of QR Codes QR codes, short for Quick Response codes, have seamlessly integrated into our daily lives, offering a convenient way to access information with a simple scan. But beneath their surface lies a potential threat – are QR codes really safe for users? Understanding the…
-
The Truth About AI’s End
by
Demystifying the Doom and Gloom: AI and Public Perception When it comes to the public narrative about artificial intelligence, the stories of doom and gloom can be a bit misleading. From the perspective of experts, the fear surrounding AI is steeped in society and perpetuated by the deep-seated concern of nonhuman intelligence taking over and…
-

Hacker Takes Down Internet in 30 Mins
by
Joe Grand: From Hacker to Ethical Superhero Joe Grand, once a notorious hacker, has transformed into a real-life ethical superhero. His journey from delinquent hacker to a force for good is an inspiring story of redemption and dedication to helping others. Let’s dive into the details of Joe’s incredible transformation and how he uses his…
-

ATM Skimmer Hack Revealed!
by
The Problem of ATM Skimming: A Closer Look ATM skimming is a serious problem that affects millions of people around the world. Criminals use skimming devices to steal sensitive information from unsuspecting ATM users, putting their financial security at risk. Understanding how these devices work is essential for protecting oneself from fraud. Read on to…
-

Sumsub Hacker Strikes: Change Your Passwords Now!
by
Protecting Your Online Security When a security researcher from Canada stumbled upon a leaked password from an unknown individual, they immediately reached out to warn the person about the potential risks. This unexpected encounter with a white hat hacker shed light on the importance of maintaining strong password security in an era dominated by cyber…
-

Uncovering ATM Skimmer in Vienna
by
Finding an ATM Skimmer: A Cautionary Tale While using an ATM machine in Vienna, a vigilant individual discovered a potential skimmer device attached to the machine. This incident serves as a sobering reminder to always be wary of cyber threats and to remain proactive in safeguarding personal information. An Unsettling Discovery Upon approaching the ATM,…
-
Uncovering the Real ‘Wolf of Wall Street’ Fraudster
by
The Truth Behind ‘The Wolf of Wall Street’ 🎥 Did you know that the blockbuster film ‘The Wolf of Wall Street’ was funded by one of the biggest anti-money laundering and corruption cases in history? Let’s dive into the shocking truth behind the world’s biggest financial fraud and the real fraudster who made it all…
-
ATM Hackers: How They Did It
by
The Circuit Board that Hacked 7 ATMs Introduction The use of a simple electronic circuit board to hack seven ATMs has caused quite a stir in the security and financial worlds. This method is an ingenious yet alarming example of how technology can be exploited for criminal activities. The Hack Criminals bypassed the physical security…
-

Hiring a Real Hacker to Hack Our Email
by
Delving into the World of Email Hacking In a daring and eye-opening experiment, a team of professionals took the plunge into the intricate world of email hacking. Through a controlled and informative demonstration, they sought to highlight the potential dangers and vulnerabilities in the realm of email security. Setting the Trap The team’s strategy involved…